My Requirement is to generate authorization code without any manual intervention similar to that requirement ( Similar Problem : Does grant_type=authorization_code always require a manual intervention for providing username/password - Questions / OAuth/OIDC - Okta Developer Community ) .
After going through this document, I found there is one way
Get session Token (Already done)
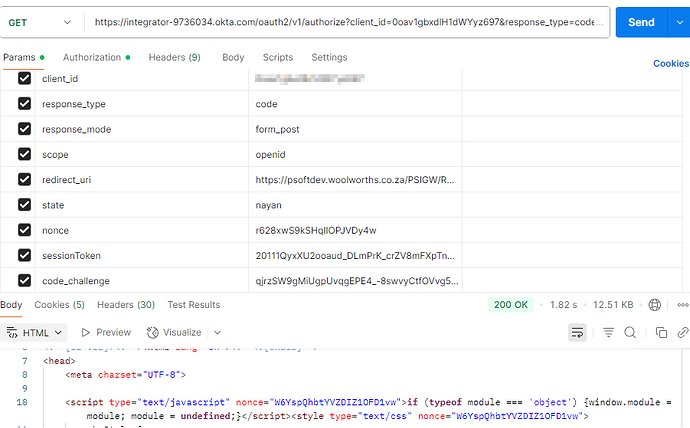
Generate Perform the /authorize call using the sessionToken and setting the reponse_type=code (Unable to get this code)
Generate Token for this Authorization code (not done yet).
I am not able to generate Authorization code as per 2nd step getting some other output in HTML format.
Can any one guide me please
vk-giri
September 12, 2025, 8:13am
2
Hi,
You can check out this article - Okta Help Center (Lightning) to get the tokens in Auth Code flow without manual intervention.
FYI, you would also need to modify your policies so that Passwords are the only factor required for the flow.
Hi , I am looking to generate Authorization_code without Manual intervention, where I found this documentation provided by octa (How to Get Tokens for an OIDC Application without a Browser Using Curl/Postman ) but I am not getting expected result in the 2nd step.
andrea
September 12, 2025, 11:11pm
4
Do you see any errors returned when you try to exchange the sessionToken for an authorizationCode, for example an error that says “login_required”? If a 200 response is being returned, you’ll need to check the actual page to see if an error is returned or you could check your Okta System Log for any failures for the OIDC app in question.
Hi @anderaanderaanderaanderaanderaanderaanderaandera
No , I can’t see any such error it is giving me 200 OK .
Actually, I have followed this documentation accordingly (How to Get Tokens for an OIDC Application without a Browser Using Curl/Postman ) but not getting the authorization_code as per mentioned in the document in 2nd step.
It is giving me HTML response without any code .
andrea
September 15, 2025, 4:09pm
7
If you create a test policy for this user/use case that doesn’t require MFA verification, are you able to complete the flow?
Hi @andrea
Thanks for your continuous support .
Are you expecting user will sign in Without MFA.
is that below documentation can support me to set up ?
Bypass MFA for a Specific Set of Users
andrea
September 17, 2025, 3:45pm
9
Yes, that article should help you ensure the user will only be challenged for their Password. You may also need to double check the Global Session Policy in your org to ensure that it also will allow a user in with only a single factor/just their password, as in this article: How to Prompt for Password Only when Logging In to Okta (OIE)
Hi @andrea Thanks for your support.
After putting a lot of effort, we got authorization code & with that Access token.
1 Like
system
September 24, 2025, 10:49am
11
This topic was automatically closed 24 hours after the last reply. New replies are no longer allowed.